How TLS handshake works
This chart is based on the article here:
https://www.cloudflare.com/learning/ssl/what-happens-in-a-tls-handshake/
It would be much clear to be able to show it in a sequence chart. The key point is in each step what client/server has to generate sessionKey.
The premasterSecret is the key factor here. it got generated in the client side by using the pubic key generated in server side. In this way, client side has it’s value (since it generated in client side) and the server side can get it by using private key to decrete it.
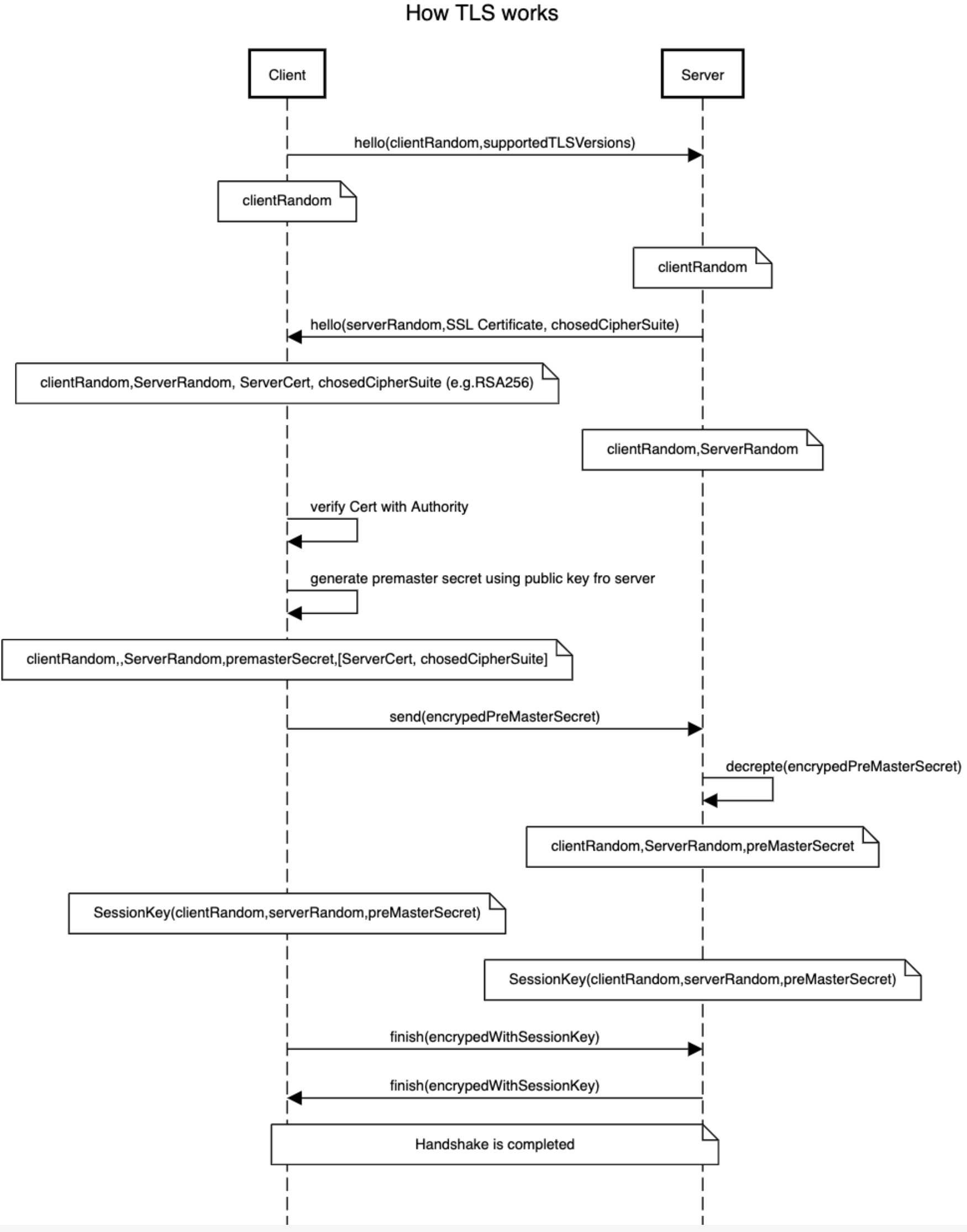
Sequence diagram source code:
title How TLS works
Client->Server:hello(clientRandom,supportedTLSVersions)
note over Client:clientRandom
note over Server:clientRandom
Server->Client:hello(serverRandom,SSL Certificate, chosedCipherSuite)
note over Client:clientRandom,ServerRandom, ServerCert, chosedCipherSuite (e.g.RSA256)
note over Server:clientRandom,ServerRandom
Client->Client: verify Cert with Authority
Client->Client: generate premaster secret using public key fro server
note over Client:clientRandom,,ServerRandom,premasterSecret,[ServerCert, chosedCipherSuite]
Client->Server:send(encrypedPreMasterSecret)
Server->Server:decrepte(encrypedPreMasterSecret)
note over Server:clientRandom,ServerRandom,preMasterSecret
note over Client: SessionKey(clientRandom,serverRandom,preMasterSecret)
note over Server: SessionKey(clientRandom,serverRandom,preMasterSecret)
Client->Server:finish(encrypedWithSessionKey)
Server->Client:finish(encrypedWithSessionKey)
note over Client,Server:Handshake is completedmTLS
mutual TLS is enhanced TLS which server side needs to verify the identity on the client side as well. The main difference is we need a new server generated preMasterSecret to generate the session key.
2 Comments
liangqi
Sequence Diagram website: https://sequencediagram.org/
liangqi
I am not exactly sure why not just use the preMasterSecret to generate sessionKey? for security reason for sure just I am not sure the exactly case we need them.